Project Overview
Conducted a comprehensive Splunk implementation project as part of advanced cybersecurity coursework at Kingston University. Worked as the lead technical analyst responsible for log analysis and security monitoring across diverse system infrastructure. This practical application involved working extensively with machine-generated logs to identify security vulnerabilities, detect suspicious network activities, and present findings through data visualisations.
Technologies Utilised
Analytics Platform
Splunk Enterprise, Splunk Universal Forwarders
Log Sources
Linux, Spark, Mac, HDFS, OpenSSH
Query Languages
Splunk Search Processing Language (SPL), Regular Expressions
Data Visualisation
Developed complex dashboard visualisations to present key security findings in accessible formats
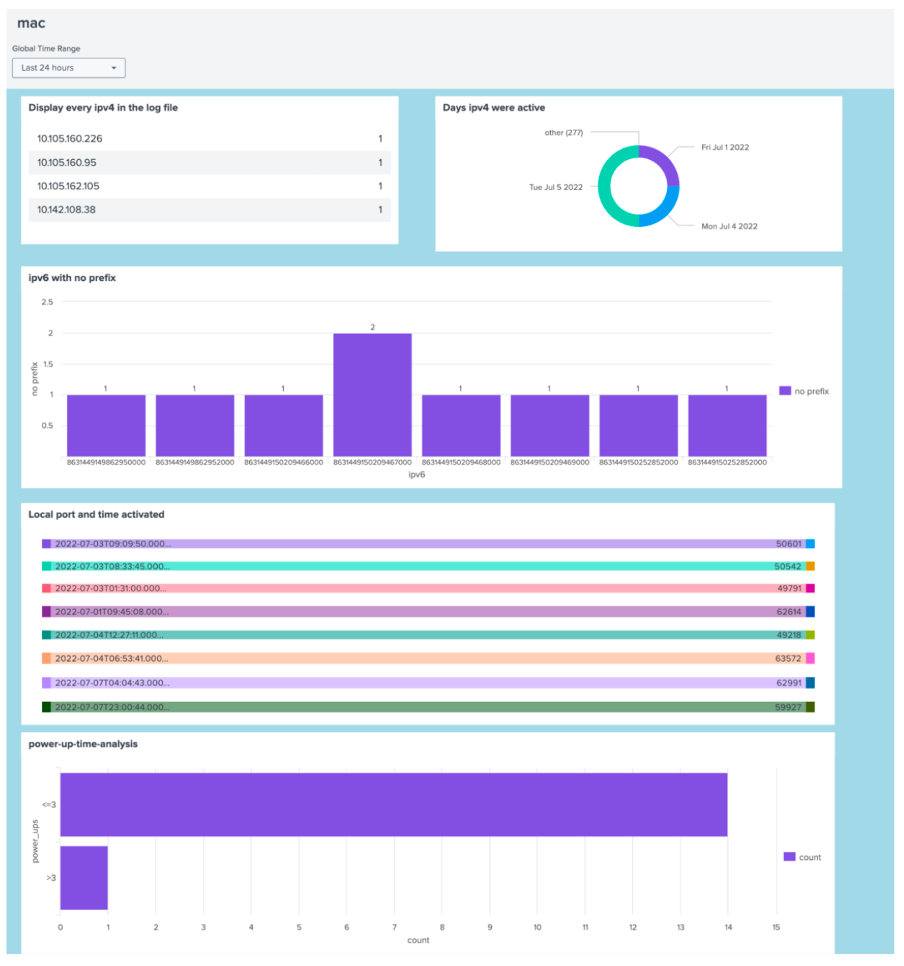
Infrastructure
TCP/IP networking, data collection points, indexers
Key Technical Contributions
Advanced Log Analysis
- Engineered 25 distinct Splunk queries using regex extraction, statistical functions, and time-based analysis
- Developed visualisation dashboards for Linux, Spark, Mac, HDFS, and OpenSSH log sources
- Identified critical security patterns including abnormal authentication attempts and suspicious IP connections
- Applied correlation techniques to detect multi-stage attack patterns across diverse log sources
Security Monitoring Implementation
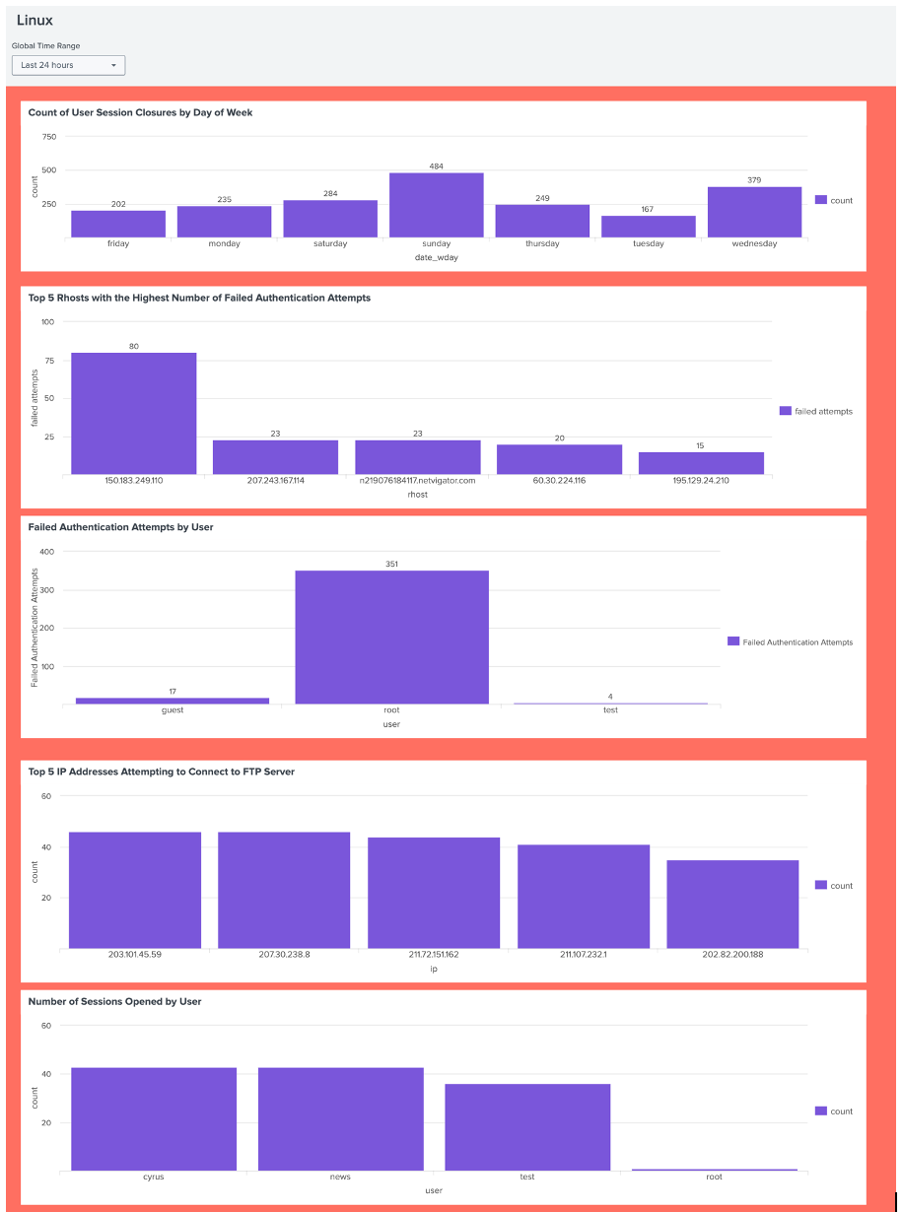
- Tracked failed authentication attempts by users and IP addresses to identify potential security issues
- Analysed network connections, highlighting unusual FTP server access attempts
- Detected patterns of invalid users and authentication failures by geographic origin
- Created time-based visualisations to establish baseline activity and highlight anomalous events
Data Collection Infrastructure
- Successfully configured Splunk Universal Forwarders for secure data transmission
- Established TCP-based collection points for centralised log aggregation
- Configured indexers for efficient processing of security-relevant log data
- Implemented appropriate authentication mechanisms for data transmission
Dashboard Development
- Created five comprehensive dashboards with custom visualisations for different log sources
- Designed interfaces allowing for clear interpretation of complex security data
- Implemented time-based charts to display security event trends and patterns
- Developed filterable views enabling dynamic exploration of security incidents
Selected screenshots from my security analytics and Splunk implementation work. Extensive additional dashboards, search queries, and analysis reports from more complex security scenarios are available for review by potential employers.

Security Monitoring Dashboard
Multi-panel view tracking authentication failures and suspicious access patterns
Advanced Log Analysis
Statistical visualisation of security events across diverse system types
Authentication Analysis
Tracking failed login attempts with geographic origin mapping
Network Anomaly Detection
Identifying unusual network traffic patterns and potential intrusion attempts
Project Outcomes
Comprehensive Log Analysis
Successfully analysed over 10,000 log entries across five diverse system types
Vulnerability Identification
Identified numerous potential security vulnerabilities through pattern recognition
Improved Response Time
Demonstrated how real-time monitoring could reduce security incident detection time
Enhanced Visibility
Enhanced visibility into network activities across simulated systems