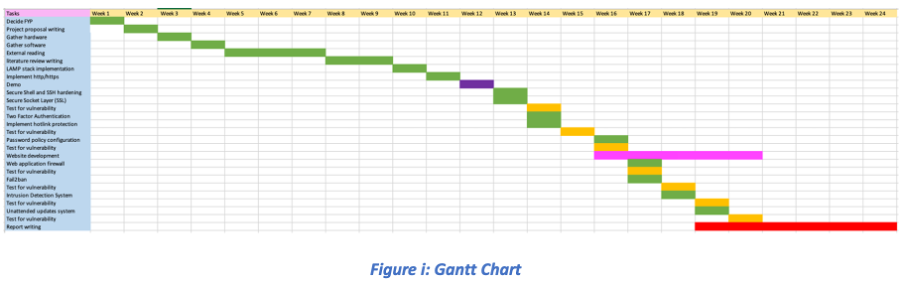
Project Aims & Objectives
The primary goal of this project was to build and test a highly secure webserver from scratch, capable of defending against cyber threats, while hosting a functional website to demonstrate practical application. I aimed to implement a comprehensive set of security measures on an Ubuntu environment and validate them through extensive testing.
Secure Server Implementation
Set up a secure webserver with SSL encryption, SSH hardening, and advanced authentication methods.
Threat Protection
Implement protection against common attack vectors using Web Application Firewall and Intrusion Detection System.
Practical Application
Develop a functional website to demonstrate the security measures in a real-world scenario.
Security Validation
Conduct thorough testing to verify that all security measures function correctly against realistic threats.
Project Overview
Comprehensive Security Architecture
This Bachelor's Final Year Project (FYP) at Kingston University involved setting up a secure webserver on an Ubuntu environment using VirtualBox. The goal was to create a highly secure yet functional server that could withstand various cyber threats while hosting a real website. I implemented multiple layers of security, from SSL encryption and SSH hardening to intrusion detection and brute-force protection.
To demonstrate the practical application of this secure environment, I developed gojogym.com, a functional gym website with user authentication, booking capabilities, and database integration—all protected by the robust security measures implemented on the server. The project received an A* grade, reflecting the comprehensive implementation and thorough security approach.
Tools & Technologies Used
Ubuntu Server
Operating system for hosting the secure webserver
ModSecurity
Web Application Firewall for Apache
OpenSSL
SSL/TLS encryption for secure data transmission
Fail2Ban
Intrusion prevention framework for blocking brute-force attacks
Snort
Network intrusion detection and prevention system
Two-Factor Authentication
Extra security layer using Google Authenticator
PHP & MySQL
Backend technologies for website development
VirtualBox
Virtualization platform for secure testing environment
Security Implementation Details
This project involved a comprehensive approach to server security, starting with a controlled testing environment created using VirtualBox. I set up two virtual machines: an Ubuntu 20.04.1 Server to host the webserver and a Kali Linux machine for security testing.
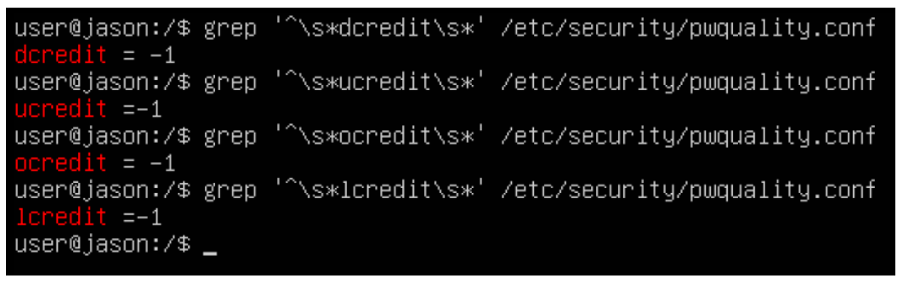
The core security measures implemented included SSL encryption with a self-signed certificate, SSH hardening with disabled root login and key-based authentication, Two-Factor Authentication for admin access, and Fail2Ban to detect and block brute-force attacks.
Advanced Security Features
Beyond the fundamental security measures, I enhanced the server's defenses with ModSecurity, a powerful Web Application Firewall that protected against common web exploits like SQL injection attacks. I also deployed Snort as an intrusion detection system to monitor and alert on suspicious network traffic.
For long-term security maintenance, I configured unattended updates to automatically apply security patches and implemented hotlink protection to prevent unauthorized access to website assets. These layered defenses created a robust security posture for the server.
SSH Hardening Implementation
A critical component of the server's security was the hardening of SSH access. I configured OpenSSH with multiple protective measures to prevent unauthorized access. This included disabling root login entirely, enforcing key-based authentication instead of passwords, changing the default SSH port, and implementing connection rate limiting.
Additionally, I integrated Google Authenticator to provide Two-Factor Authentication for SSH logins, adding an essential extra layer of security. This combination of measures made brute force attacks virtually impossible and significantly enhanced the server's access security.
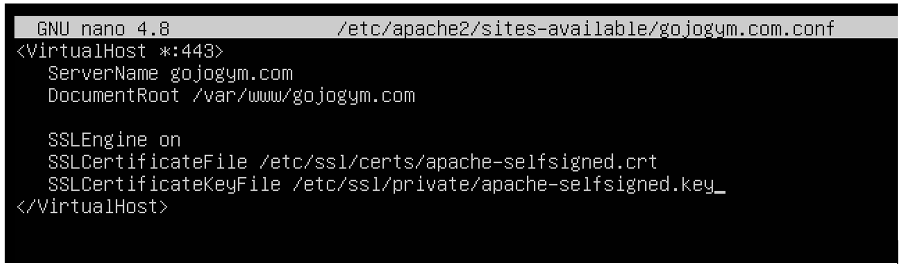
Web Application Firewall
To protect against application-level attacks, I implemented ModSecurity as a Web Application Firewall (WAF) for the Apache server. This powerful tool inspected HTTP requests and responses to identify and block malicious traffic targeting the web application.
I configured ModSecurity with the OWASP Core Rule Set to provide baseline protection against common web application attacks like SQL injection, cross-site scripting (XSS), and local file inclusion. I then fine-tuned the rules to minimise false positives while maintaining robust protection. This was essential for securing the website's user interactions and database operations.
Website Development
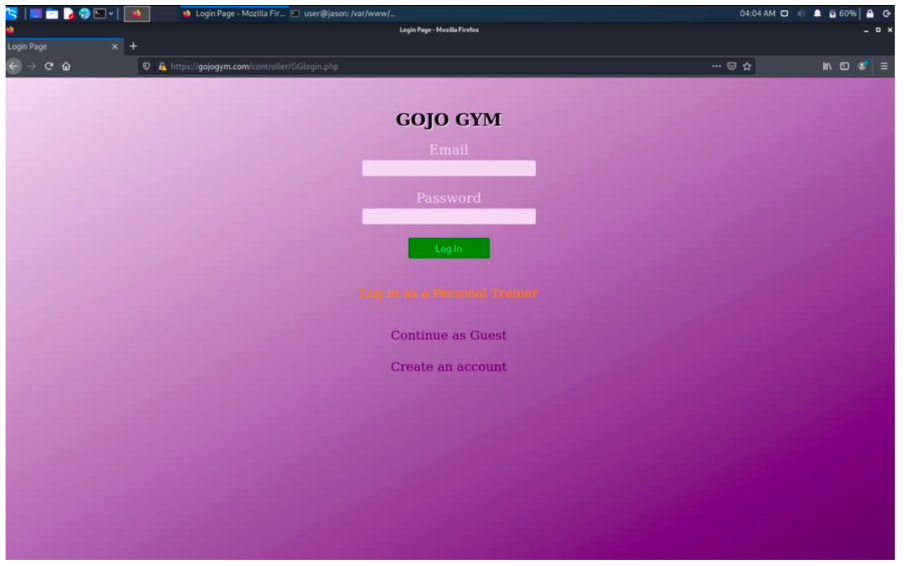
Functional Gym Website
As part of this project, I developed a fully functional gym website, gojogym.com, to demonstrate the practical application of the secure webserver. Built using PHP and integrated with a MySQL database via phpMyAdmin, the site allowed users to securely book training sessions and access gym information.
The website featured user authentication with separate dashboards for clients and trainers, a booking system for training sessions, content management for gym information, and a secure registration system for new users. All user interactions were protected by the server's security measures, including SSL encryption and Web Application Firewall protection.
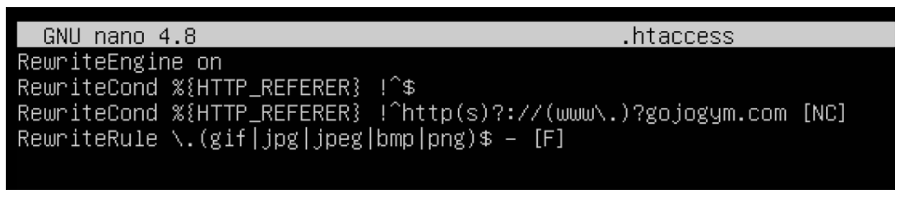
Database Security Measures
Securing the MySQL database was crucial for protecting user data on the gym website. I implemented multiple layers of database security, starting with strong password policies and restricted remote access permissions.
All database connections were made through secure channels, and I employed prepared statements and parameterised queries throughout the PHP code to prevent SQL injection attacks. User passwords were stored using strong hashing algorithms with unique salts, and database backups were regularly scheduled and encrypted to ensure data integrity and availability.
Testing and Validation
To ensure the effectiveness of the security measures, I conducted extensive testing targeting each component. I performed simulated brute-force attacks to verify that Fail2Ban correctly blocked IPs after multiple failed attempts. Vulnerability scans with Nmap showed no exploitable weaknesses, and Snort successfully detected and logged test intrusions.
I also tested website functionality to confirm that user authentication, booking systems, and data storage worked correctly while maintaining security. This comprehensive validation process verified that the server was both secure and practical for real-world use.
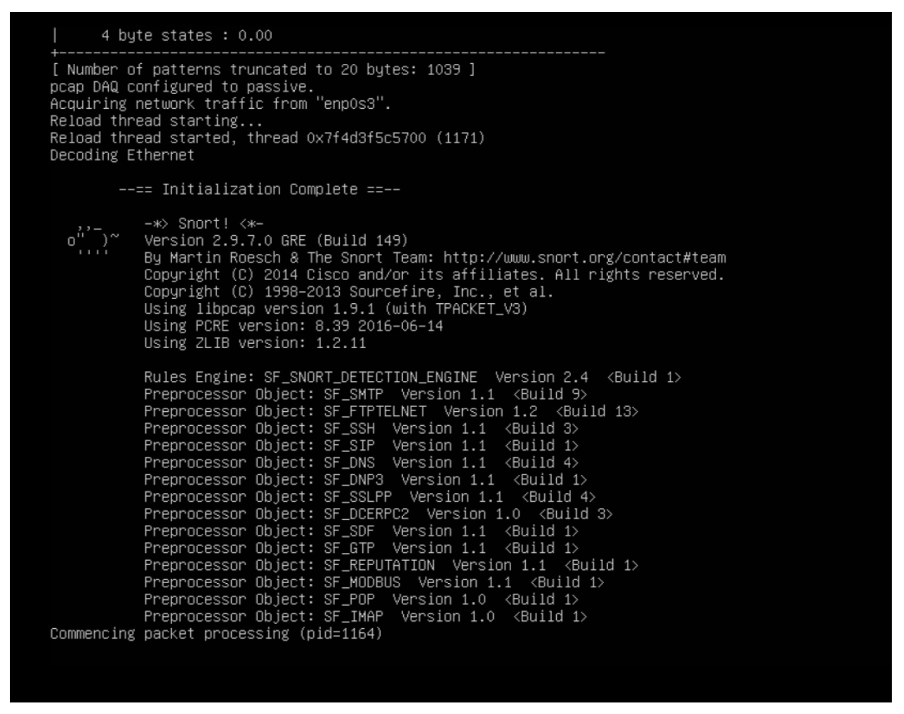
Intrusion Detection System
I deployed Snort as a network intrusion detection system (IDS) to monitor traffic for suspicious patterns and potential attacks. Snort analyzed network packets in real-time, comparing them against a database of known attack signatures to identify malicious activity.
After configuring Snort with the correct network interface (which required troubleshooting, as detailed in the challenges section), I set up custom rules to detect specific threats relevant to web servers. I also implemented logging and alerting mechanisms to notify of potential intrusions, providing a critical layer of visibility into network security events.
Key Challenges & Solutions
Challenge
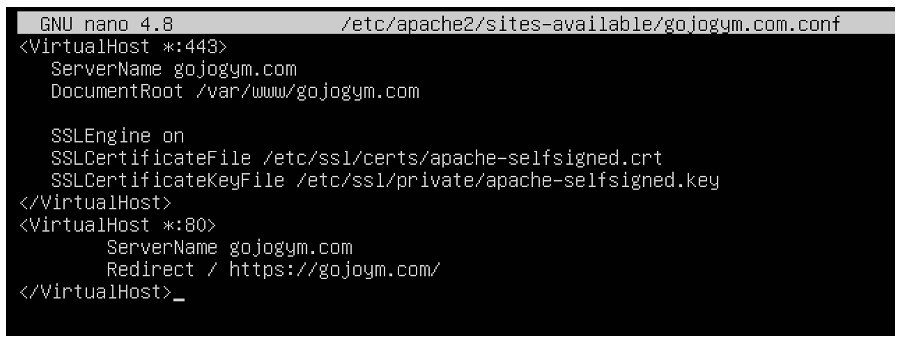
SSL Configuration Errors: Syntax errors in the Apache configuration file prevented the server from starting correctly, jeopardizing secure communication.
Solution
I consulted the Apache error logs to identify the specific lines causing the issue, corrected the syntax errors, and successfully reloaded the configuration. This enabled HTTPS traffic to function properly.
Challenge
Snort Not Detecting Traffic: The intrusion detection system initially failed to monitor network traffic, which was critical for identifying potential security threats.
Solution
Using the ifconfig command, I identified that Snort was configured with the wrong network interface. I updated the configuration to use the correct interface (enp0s3), which enabled proper traffic monitoring.
Challenge
Integrating Two-Factor Authentication: Adding 2FA to SSH logins required complex changes to both PAM and SSH configurations, with initial attempts resulting in login failures and potential lockouts.
Solution
I created a non-critical test user account to safely experiment with configurations, carefully followed documentation, and gradually implemented a working 2FA solution without risking server access.
Balancing Security and Performance
One of the key challenges in implementing comprehensive security was maintaining acceptable server performance. Security measures like SSL encryption, packet inspection, and real-time monitoring all consume system resources, potentially impacting website responsiveness.
I addressed this challenge by fine-tuning each security component, optimising Apache and MySQL configurations, and implementing caching strategies. This balanced approach allowed the server to maintain strong security while delivering responsive performance for the website users, demonstrating that security and usability can work hand-in-hand.
What I Learned
Layered Security Approach
Gained deep understanding of implementing defence-in-depth strategies with multiple security controls working together.
Linux Server Administration
Enhanced skills in configuring and managing Ubuntu servers, focusing on security hardening techniques.
Security Testing
Developed methodical approaches to testing security implementations and validating effectiveness against real threats.
Secure Web Development
Learned to build web applications with security as a fundamental design principle rather than an afterthought.
System Integration
Strengthened ability to integrate multiple security tools and technologies into a cohesive, functional system.
Performance Optimisation
Mastered techniques for balancing strong security measures with system performance requirements.
Technical Implementation Highlights
The most technically challenging aspect of this project was creating a cohesive security system where multiple defence mechanisms worked together without conflicts. For example, configuring ModSecurity rules to work alongside Fail2Ban's detection system required careful tuning to prevent unintended interactions.
I'm particularly proud of the SSL/TLS implementation, which achieved an A+ rating on SSL testing tools by implementing perfect forward secrecy, strong ciphers, and proper HSTS headers. These technical details demonstrate not just functional security, but security implemented according to industry best practices.
Results & Impact
Robust Security Implementation
Created a highly secure webserver capable of defending against common cyber threats and hosting functional applications.
Successful Threat Prevention
All simulated attacks and vulnerability tests were successfully detected and blocked by the implemented security measures.
Practical Application
Developed a fully functional gym website that utilized the security features while maintaining good user experience.
Skills Development
Significantly enhanced my expertise in cybersecurity, server administration, and secure web development.